How to scan Linux for rootkits with rkhunter
Last updated on September 24, 2020 by Dan Nanni
A rootkit is a malicious software designed to obtain root-level access to a computer while hiding its presence or identity from antivirus software. Common ways for rootkits to get installed on your system are through trojan horses contained in drive-by downloads, known system vulnerabilities, suspicious email attachments, web surfing, or simply by password cracking.
On Linux, there are several rootkit scanner tools that help project against known or potential rootkits. One such rootkit detection tool is called Rootkit Hunter (rkhunter). Here I will describe how to scan a Linux system for rootkits with rkhunter.
Install rkhunter on Linux
To install rkhunter or Ubuntu, Debian or Linux Mint:
$ sudo apt-get install rkhunter
To install rkhunter on Fedora:
$ sudo yum install rkhunter
To install rkhunter on CentOS or RHEL, first set up Repoforge repository on your system, and then use yum command.
$ sudo yum install rkhunter
Scan a Linux System for Rootkits
To perform rootkit scanning on your system, simply run the following.
$ sudo rkhunter -c
Once rkhunter is initiated, it will go ahead and run a series of tests as follows.
- Compare SHA-1 hashes of system binaries against known good values maintained in the database.
- Check for known rootkit files and directories, as well as rootkit strings.
- Perform malware detection, including checking for login backdoors, sniffer log files, and other suspicious directories.
- Perform trojan specific checks such as examining enabled xinetd services.
- Perform checks on network ports and interfaces.
- Perform system boot checks.
- Perform group and account checks.
- Perform system configuration file checks.
- Perform filesystem checks.
The following screenshots shows Rootkit Hunter in action.
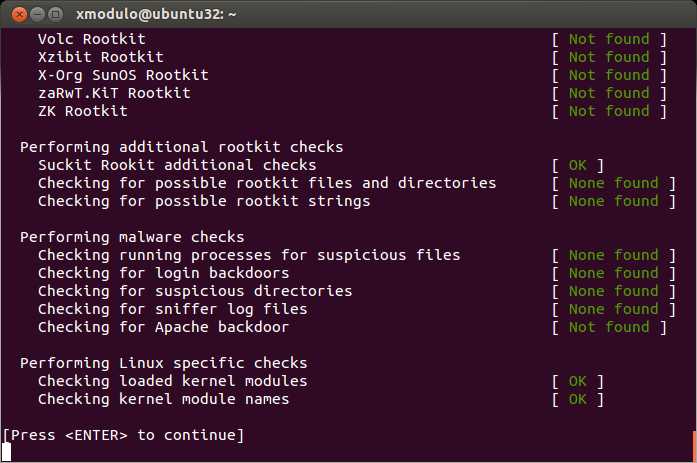
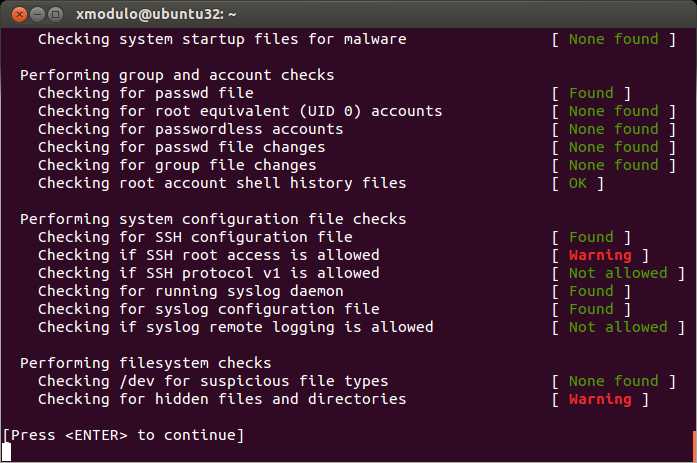
Once scanning is completed, rkhunter stores the result in /var/log/rkhunter.log. You can check for any warning as follows.
$ sudo grep Warning /var/log/rkhunter.log
[11:09:12] /usr/bin/unhide.rb [ Warning ] [11:09:12] Warning: The command '/usr/bin/unhide.rb' has been replaced by a script: /usr/bin/unhide.rb: Ruby script, ASCII text [11:10:53] Checking if SSH root access is allowed [ Warning ] [11:10:53] Warning: The SSH and rkhunter configuration options should be the same: [11:10:54] Checking for hidden files and directories [ Warning ] [11:10:54] Warning: Hidden directory found: /etc/.java [11:10:54] Warning: Hidden directory found: /dev/.udev [11:10:54] Warning: Hidden file found: /dev/.initramfs: symbolic link to `/run/initramfs'
Rootkit Hunter relies on a set of database files to detect rootkits. If you would like to check if the database files are up-to-date, simply run rkhunter with --update option. If there is a newer version of the database files, it will automatically fetch up-to-date database files using wget.
$ sudo rkhunter --update
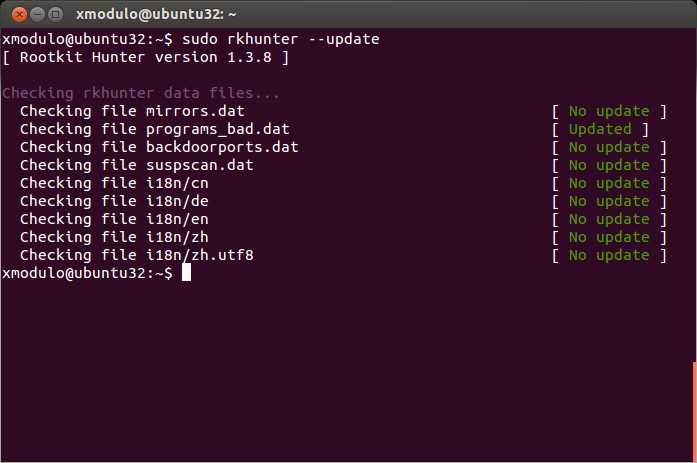
rkhunter can be run as a cron job with --cronjob option, in which case rkhunter will perform scanning in non-interactive mode, and store scanning result in /var/log/rkhunter.log for offline inspection.
As a rootkit scanner tool, rkhunter can only detect rookits, but not remove them. Then what should you do if rkhunter reports the presence of a rootkit, or throws any kind of warnings? First, you need to check whether or not those cases are false-positives. Warnings could be triggered simply due to ongoing software upgrades, custom system configurations, or other legitimate binary changes. If you are not sure, seeking help from sources such as rkhunter user mailing list can be an option.
If your system is indeed infected with a rootkit, trying to remove the rootkit yourself may not be the best course of action, unless you are a security expert who is capable of diagnosing the full mechanism, attack vector and penetration path of the particular rootkit.
When a rootkit is discovered on your system, the best way to deal with the situation is probably taking the compromised system offline first, and then moving all your data away from the system. While doing so, do not back up any binary that you cannot confirm is clean.
Support Xmodulo
This website is made possible by minimal ads and your gracious donation via PayPal or credit card
Please note that this article is published by Xmodulo.com under a Creative Commons Attribution-ShareAlike 3.0 Unported License. If you would like to use the whole or any part of this article, you need to cite this web page at Xmodulo.com as the original source.
Xmodulo © 2021 ‒ About ‒ Write for Us ‒ Feed ‒ Powered by DigitalOcean

