How to set up VNC over SSH
Last updated on September 3, 2020 by Dan Nanni
By nature, VNC is not a secure protocol. A well-known security risk of VNC is that you connect to a VNC server via an unencrypted channel across the network. Thus anyone can snoop on an established VNC session. To protect against VNC sniffing, you should try additional out-of-band encryption mechanism, underneath or on top of VNC connections.
One such mechanism is to set up a VNC session through an SSH tunnel. In this tutorial, I will describe how to set up VNC over SSH on Linux.
I assume that you already have a VNC server to connect to set up somewhere on the network.
In order to create an SSH tunnel to a remote host where a VNC server is running, the remote host needs to have SSH server running as well. Thus first install OpenSSH server on the remote host.
The next step is to create an SSH tunnel from a local host to the remote host. In order to do so, run the following command. Here 5900 is the port number which a remote VNC server is listening on.
$ ssh user@remote_host -L 5900:127.0.0.1:5900
Once you enter SSH password and successfully log in, an SSH tunnel will be established between 127.0.0.1:5900 and remote_host:5900.
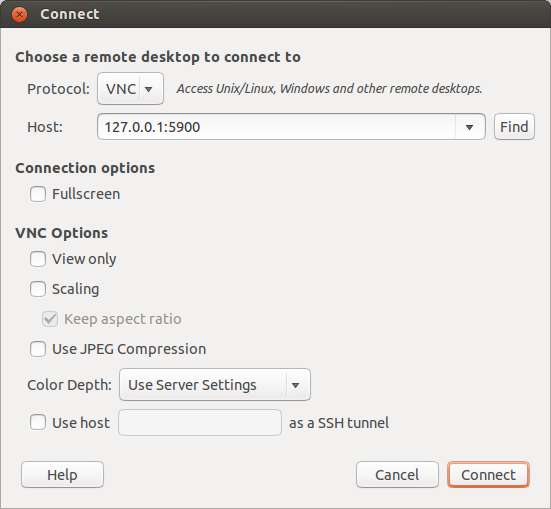
Now you can go ahead and launch VNC client from local host. On VNC client, connect to 127.0.0.1:5900, instead of the remote VNC server. The VNC traffic will then be routed over the SSH tunnel between you and the remote VNC server, and thus be securely protected from packet sniffing.
Support Xmodulo
This website is made possible by minimal ads and your gracious donation via PayPal or credit card
Please note that this article is published by Xmodulo.com under a Creative Commons Attribution-ShareAlike 3.0 Unported License. If you would like to use the whole or any part of this article, you need to cite this web page at Xmodulo.com as the original source.
Xmodulo © 2021 ‒ About ‒ Write for Us ‒ Feed ‒ Powered by DigitalOcean

