How to improve the security of Magento e-commerce website
Last updated on August 5, 2020 by Dan Nanni
Magento is an e-commerce software platform used by small businesses and leading brands, and its community edition is a freely available open-source program. Thanks to the huge collection of third-party developed plugins and themes which extend the default functionality and design, Magento is evolving into the WordPress of the e-commerce industry.
However, the growing popularity of Magento gives hackers a good enough reason to target this e-commerce platform. Especially when you are operating an e-shop using Magento, you are dealing with potentially important and sensitive information about your customers, which is incredibly valuable commodity to hackers. Thus it is imperative that you perform thorough due diligence and follow best practices to secure every part of your Magento deployment.
In this tutorial we will cover best practices for Magento security and demonstrate some examples on how to secure your Magento website.
1. Choose a strong and secure password for the Magento administrator account
The most obvious first step to keep your Magento installation safe and secure is to have a strong password for your Magento administrator account. Make sure that the administrator's password is at least ten random characters long and include numbers, upper and lower case letters and special characters (e.g., "q&t:A;-Q&4'?>#6"). Delete any other accounts that you're not using. The less accounts you have, the less opportunities hackers will have.
2. Use an encrypted connection (SSL/HTTPS) for all Magento web pages
SSL is a secure protocol which encrypts the sensitive information, such as login credentials, personal information etc. sent from the web browser to the web server. To implement SSL on your Magento website, first obtain an SSL certificate (e.g., from Let's Encrypt). With the obtained certificate, configure the web server to listen on port 443 and enable SSL through the Magento administration back-end.
For example, if you use Apache on a Debian based server, create a new virtual host:
# vi /etc/apache2/sites-available/your-domain.com-ssl.conf
Add the following lines to it:
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName your-domain.com
DocumentRoot /var/www/html/magento/
SSLEngine on
#Specify the path to your SSL certificate file:
SSLCertificateFile /etc/apache2/ssl/your-domain.crt
#Specify the path to private key file:
SSLCertificateKeyFile /etc/apache2/ssl/your-domain.key
#Specify the path to CA certificate:
SSLCACertificateFile /etc/apache2/ssl/ca-bundle.crt
<Directory /var/www/html/magento>
Options -Indexes +FollowSymLinks +MultiViews
Order allow,deny
AllowOverride All
</Directory>
ErrorLog /var/log/apache2/ssl_error.log
CustomLog /var/log/apache2/ssl_access.log combined
</VirtualHost>
</IfModule>
Enable the mod_ssl Apache module:
# a2enmod ssl
Disable the default SSL virtual host and enable the your-domain.com-ssl.conf virtual host:
# a2dissite default-ssl # a2ensite your-domain.com-ssl.conf
Finally restart Apache for the changes to take effect:
# /etc/init.d/apache2 restart
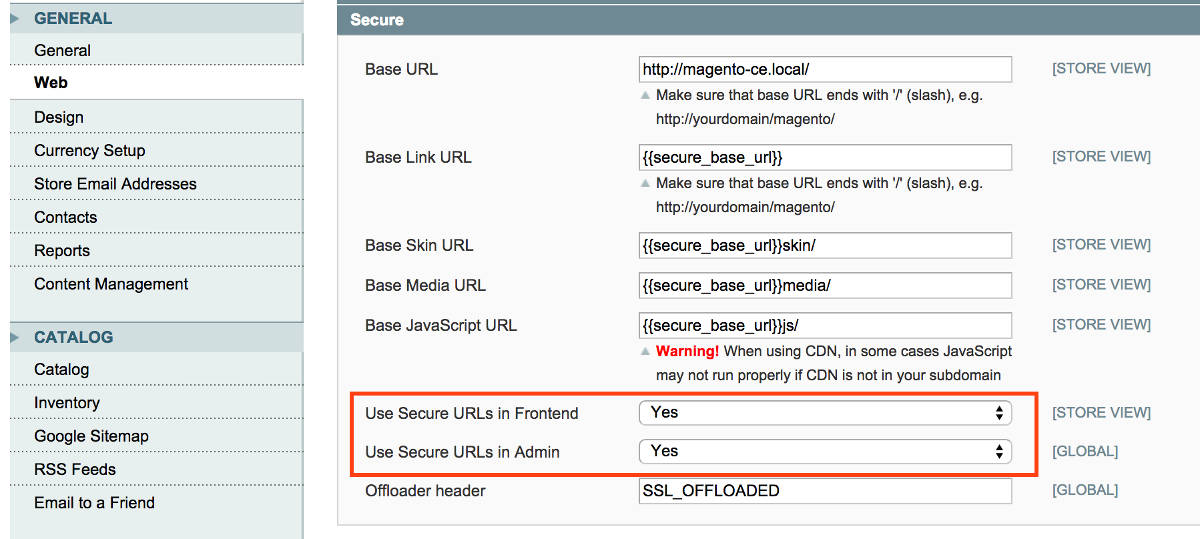
Log in to the Magento administration back-end, then go to System >> Configuration. From the menu on the left, under the General selection list, click Web. On the Secure tab change http to https, and set "Use secure URLs in Frontend" and "Use secure URLs in Admin" to Yes. Do not forget to clear the Magento cache and your web browser's cache, then try to access your website with https.
If some of your visitors bookmarked your website using http://your-domain.com and you want to make sure that all requests to http are being redirected to https, you may add the following lines to the .htaccess file located in the document root of your Magento website (e.g. /var/www/html/magento/.htaccess):
RewriteCond %{HTTPS} off
RewriteRule ^(.*)$ https://your-domain.com/$1 [R=301,L]
3. Create a custom path for the administrator back-end
The default admin URL for Magento (e.g., yourstore.com/store/admin) can become an easy target for hackers trying to break into the Magento backend using brute-force attacks. To prevent that, you can customize the default admin path as follows.
Log in to your server via SSH as root. Then open the local.xml file located in the /app/etc directory of your Magento installation (e.g. /var/www/html/magento/app/etc/local.xml), and locate the following line:
<![CDATA[admin]]>
Replace admin to something more complex, like MyMagento123 or whatever you want the URL of the administrator back-end to be. This will change the admin URL to yourstore.com/store/MyMagento123.
4. Whitelist only approved IP addresses for admin access
Besides hiding the admin URL like above, you can restrict the access to the admin URL at the network level. In other words, restrict the admin access to only a few IP addresses or CIDR blocks that you explicitly approved. To set up an IP whitelist for Apache, add the following LocationMatch directive inside your virtual host configuration. Note that MyMagento123 is the custom admin login page that you define earlier.
<LocationMatch "MyMagento123"> Order Deny,Allow Deny from All Allow from 111.111.111.0/24 </LocationMatch>
Don't forget to restart Apache after updating the whitelist. Now you will be able to access the custom admin login page (yourstore.com/store/MyMagento123) only from the specified IP address block.
5. Harden your Magento website's file permissions
Following the principle of least privilege, make sure that the Magento website files and directories are not writable by any one else except the web server. For this, the web server user (www-data on Debian, or apache on CentOS) needs to have access to Magento website files and directories under the Magento website document root, so run the following command to accomplish that (on Debian):
# chown www-data:www-data -R /var/www/html/magento
Set "chmod 750" on directories and 640 on all website files, except app/etc, media and var directories, which need 770 permissions (The 770 permissions give full control to the owner and the group, and no permissions to anyone else):
# find /var/www/html/magento -type f -print0 | xargs -r0 chmod 640
# find /var/www/html/magento -type d -print0 | xargs -r0 chmod 750
# chmod -R g+w /var/www/html/magento/{app/etc,media,var}
6. Use two-factor authentication for admin access
There is no such thing as a silver bullet as far as security is concerned. In that regard, an additional layer of protection you can add to the admin access is two-factor authentication. With two-factor authentication extension enabled, you will be required to present a one-time security code to gain access to the Magento backend. One-time security code is generated by Google Authenticator app installed on your smartphone which a malicious hacker would not possess.
7. Use Magento extensions only from trusted sources
The security of any software system is as strong as its weakest link. While the huge ecosystem of third-party Magento extensions is certainly a boon to Magento users, each of these extensions could potentially introduce a new attack vector. Even with all other security protections in place, it takes only a single vulnerability of one poorly written extension to break down your Magento system. Before integrating any third-party extension to your Magento store, always do your due diligence checking out the reputation of the developer and customer reviews from independent communities such as Magento community. Use only those extensions from reputable sources with a good track record, and those which are regularly updated and maintained.
8. Update Magento on regular basis
Keep the Magento installation including all extensions and themes up to date by upgrading whenever a new security patch or version comes out. It's a good idea to create a backup of your Magento website files and its database before you start updating Magento.
To find out which Magento version is currently installed on your website, log in to your server via SSH as root, navigate to the document root directory of your Magento based website (e.g. /var/www/html/magento) and run the following commands:
# cd /var/www/html/magento # php -r "include 'app/Mage.php'; echo 'Your Magento version is: ', Mage::getVersion(); " ; echo "";
Conclusion
In this tutorial, we discuss best security practices for Magento-powered e-commerce websites. Following these guidelines, you will substantially improve the security of your Magento website. There are other techniques you can use outside your Magento configuration to improve the general security of your website, like blocking unwanted IP addresses or installing an IDS, so be sure to do everything you can. Generally, it's better to host an e-shop on a VPS or a dedicated server rather than on a shared hosting. You will have better performances and you will have more control over your host if you are using a VPS or dedicated hosting. Whatever you do, be careful when configuring your Magento. Remember that one small mistake can break your whole Magento installation.
Support Xmodulo
This website is made possible by minimal ads and your gracious donation via PayPal or credit card
Please note that this article is published by Xmodulo.com under a Creative Commons Attribution-ShareAlike 3.0 Unported License. If you would like to use the whole or any part of this article, you need to cite this web page at Xmodulo.com as the original source.
Xmodulo © 2021 ‒ About ‒ Write for Us ‒ Feed ‒ Powered by DigitalOcean

