How to ping a specific port of a remote host
Last updated on January 13, 2020 by Dan Nanni
ping is a networking utility used to test the reachability and round-trip time (RTT) delay of a remote host over Internet Protocol (IP). The ping utility does so by sending out a series of Internet Control Message Protocol (ICMP) echo request packets to a remote host, and waiting for corresponding ICMP response packets from the host. However, you cannot probe a specific port with ping command because ICMP belongs to layer-3 IP layer, not layer-4 transport layer (e.g., TCP/UDP).
In order to ping a specific port of a remote host, you need to use layer-4 transport protocols which have a notion of port numbers.
There are many command-line tools in Linux that read from and write to network connections using TCP or UDP. You can use some of these tools to ping a remote port, as described below.
Method One: nmap
nmap is a network mapper utility used to check the availability of hosts and their services. Using nmap, you can check whether a specific TCP/UDP port of a remote host is open or not.
To ping a TCP port of a remote host using nmap:
$ nmap -p 80 -sT www.xmodulo.com
Starting Nmap 5.00 ( http://nmap.org ) at 2012-08-29 13:43 EDT Interesting ports on www.xmodulo.com: PORT STATE SERVICE 80/tcp closed http Nmap done: 1 IP address (1 host up) scanned in 0.14 seconds
To ping a UDP port of a remote host using nmap:
$ sudo nmap -p 80 -sU www.xmodulo.com
Starting Nmap 5.00 ( http://nmap.org ) at 2012-08-29 13:47 EDT Interesting ports on www.xmodulo.com: PORT STATE SERVICE 80/udp closed http Nmap done: 1 IP address (1 host up) scanned in 0.11 seconds
Note that unlike TCP case, you need root privilege to send out raw UDP packets using nmap.
Method Two: netcat
netcat is another powerful tool, nicknamed as swiss-army knife of networking. Among its rich features, netcat can do port scanning as follows.
To ping a TCP port of a remote host using netcat:
$ nc -zvv mit.edu 80
DNS fwd/rev mismatch: mit.edu != WEB.MIT.EDU mit.edu [18.9.22.69] 80 (www) open sent 0, rcvd 0
To ping a UDP port of a remote host using netcat:
$ nc -zuvv mit.edu 80
DNS fwd/rev mismatch: mit.edu != WEB.MIT.EDU mit.edu [18.9.22.69] 80 (www) open sent 0, rcvd 0
Method Three: paping
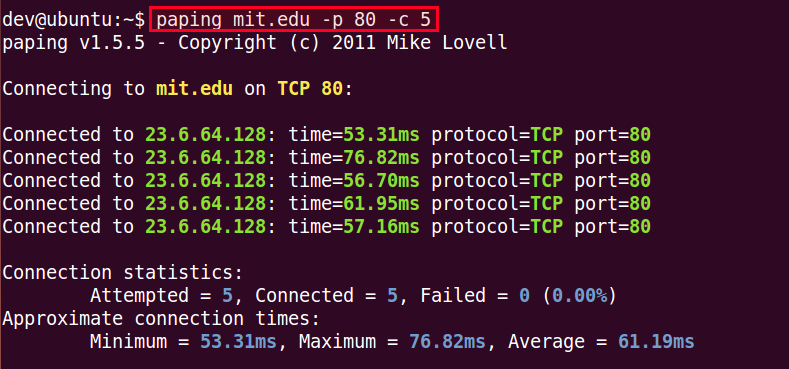
The above tools so far only check whether a given port number is open or closed, but do not measure the RTT delay, like in the original ping utility. If you would like to actually measure network latency as well, you can use paping, which is a cross-platform TCP port testing tool.
$ paping mit.edu -p 80 -c 3
Method Four: tcpping
Similar to paping, tcpping can also measure RTT network delay against an open TCP port of a remote server.
$ sudo tcpping www.cnn.com seq 0: tcp response from 157.166.240.13 [open] 82.544 ms seq 1: tcp response from 157.166.241.10 [open] 80.771 ms seq 2: tcp response from 157.166.241.11 [open] 80.838 ms seq 3: tcp response from 157.166.241.10 [open] 80.145 ms seq 4: tcp response from 157.166.240.11 [open] 86.253 ms
Support Xmodulo
This website is made possible by minimal ads and your gracious donation via PayPal or credit card
Please note that this article is published by Xmodulo.com under a Creative Commons Attribution-ShareAlike 3.0 Unported License. If you would like to use the whole or any part of this article, you need to cite this web page at Xmodulo.com as the original source.
Xmodulo © 2021 ‒ About ‒ Write for Us ‒ Feed ‒ Powered by DigitalOcean

